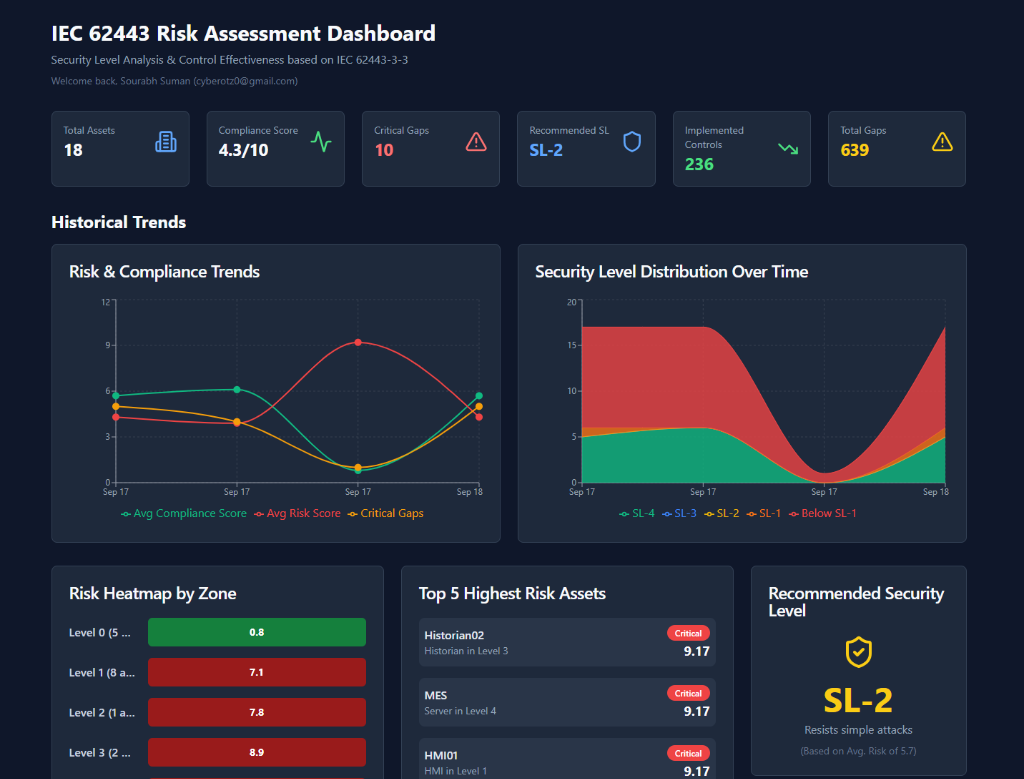
See Your Dashboard in Action
Real-time IEC 62443 compliance scoring with visual risk analytics
Visual Analytics
Interactive charts and heat maps
Security Levels
IEC 62443 SL-1 through SL-4
Gap Identification
Prioritized critical gaps
Trend Analysis
Historical compliance tracking