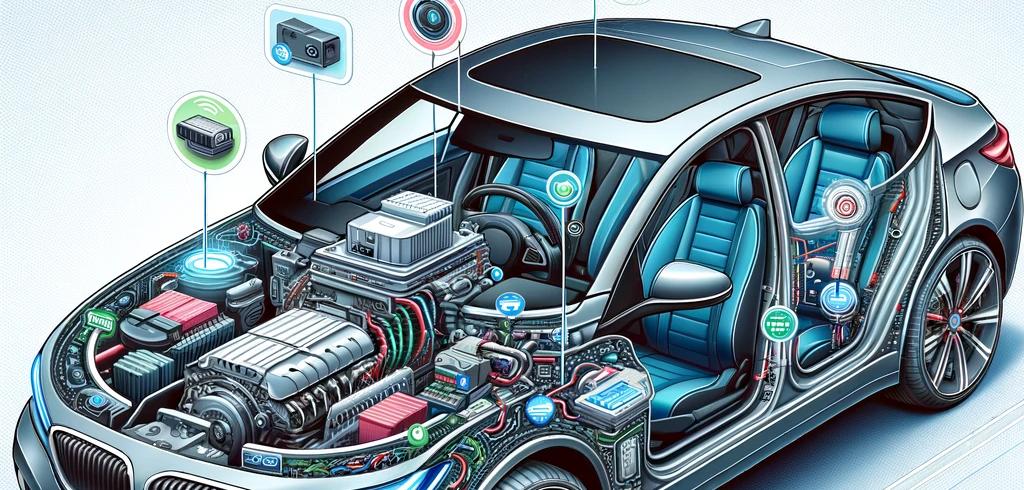
Introduction
In the age of connected and autonomous vehicles, cybersecurity has emerged as a critical concern. Modern cars, equipped with advanced software and connectivity features, present new opportunities for cyber threats. This article delves into the software-driven components of cars, their communication protocols, the level of their security, the standards they follow, and the recommendations of ISO 21434 for enhanced security. We also explore the potential consequences of inadequate cybersecurity measures in vehicles.
Software-Driven Components in Cars
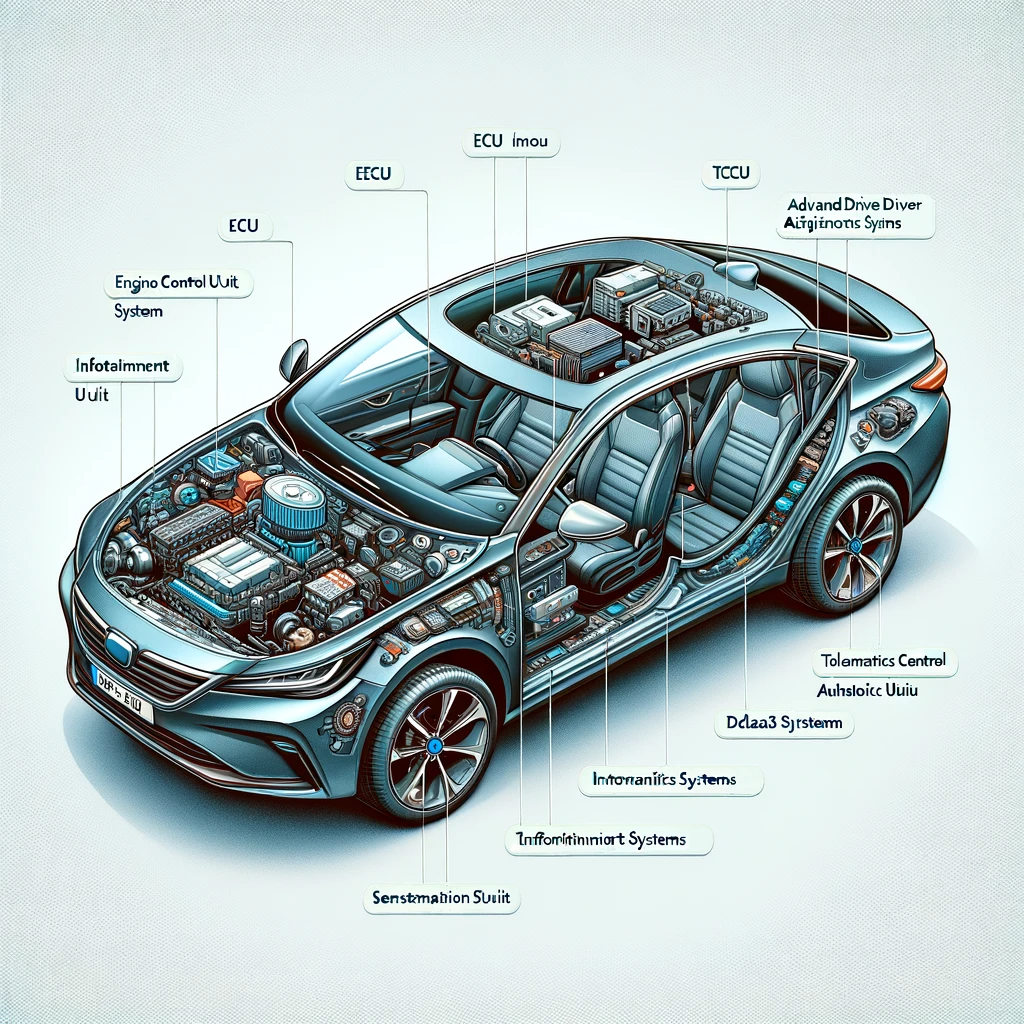
Engine Control Unit (ECU)
- Function: Controls engine functions like fuel injection and ignition timing.
- Communication: Utilizes CAN (Controller Area Network) and OBD-II (On-Board Diagnostics) protocols.
- Data: Engine performance data, diagnostic trouble codes.
Infotainment Systems
- Function: Provides navigation, media playback, and connectivity features.
- Communication: Bluetooth, Wi-Fi, USB, and sometimes cellular networks.
- Data: User preferences, location data, connected device information.
Advanced Driver Assistance Systems (ADAS)
- Function: Offers features like adaptive cruise control, lane-keeping assist, and parking assistance.
- Communication: Primarily CAN, with some radar and LiDAR data transmission.
- Data: Proximity data, camera images, sensor readings.
Telematics Control Unit (TCU)
- Function: Enables vehicle tracking, remote diagnostics, and emergency services.
- Communication: Cellular networks and GPS.
- Data: Vehicle location, speed, and diagnostic data.
Security and Standards
Modern vehicles, while sophisticated, are not entirely immune to cybersecurity threats. The interconnected nature of these components makes them vulnerable to hacking, data breaches, and unauthorized control.
Cybersecurity Standards
- ISO/SAE 21434: A global standard providing guidelines for automotive cybersecurity risk management. It focuses on product development, production, operation, maintenance, and decommissioning of electrical and electronic (E/E) systems in road vehicles.
- Automotive SPICE: A framework for designing and assessing software development processes.
- SAE J3061: Provides guidelines for cybersecurity processes throughout the lifecycle of the vehicle.
Security Measures
- Encryption: Protects data communication.
- Authentication and Authorization Protocols: Ensures that only authorized entities can access or control vehicle systems.
- Regular Software Updates: Addresses vulnerabilities and enhances system security.
The Role of ISO 21434
ISO 21434 recommends a holistic approach to automotive cybersecurity, encompassing:
- Risk Assessment: Identifying potential threats and vulnerabilities.
- Design and Engineering: Integrating security into the design of E/E systems.
- Verification and Validation: Testing security measures.
- Incident Response: Establishing procedures to respond to cybersecurity incidents.
Potential Consequences of Inadequate Security
- Unauthorized Vehicle Control: Hackers could potentially take control of vehicle functions, posing a danger to occupants and others.
- Data Breaches: Personal information stored in the vehicle’s systems could be compromised.
- Financial Losses: Costs associated with data breaches, system repairs, and legal liabilities.
- Reputation Damage: A major cybersecurity incident can erode consumer trust in a brand.
Conclusion
The integration of sophisticated software in modern vehicles brings convenience and innovation but also necessitates robust cybersecurity measures. Standards like ISO 21434 play a crucial role in guiding manufacturers towards safer automotive designs. As technology evolves, so must the cybersecurity strategies to protect these increasingly connected vehicles. The stakes are high – a compromised vehicle can have dire consequences, making cybersecurity an essential component of automotive design and maintenance.